 Whether you realize it, near-field communication — or NFC — plays an integral part in how we live our daily lives, seamlessly connecting us to the world around us. Chances are, you’ve interacted with a device or service using NFC technology more times than you realize — for contactless payments, asset tracking, transit, shipping, ski passes, dry cleaning, unlocking your car or even using a passport. Anything involving identification, authentication and tracking likely leverages NFC technology in our modern world.
Whether you realize it, near-field communication — or NFC — plays an integral part in how we live our daily lives, seamlessly connecting us to the world around us. Chances are, you’ve interacted with a device or service using NFC technology more times than you realize — for contactless payments, asset tracking, transit, shipping, ski passes, dry cleaning, unlocking your car or even using a passport. Anything involving identification, authentication and tracking likely leverages NFC technology in our modern world.
In our global economy, companies face unlawful production and importation of goods from abroad. Without key oversight, unscrupulous manufacturers may create unauthorized duplicates, risking a company’s reputation and IP. Illegal counterfeit or black market goods often bear spurious and deceitful marks, labels and product content. With gray market infringement, a product has genuine trademarks but is sold through unauthorized sellers. What you purchase and what you get may be very different things. In recent years, supply chain issues have compounded these ever-increasing threats.
One efficacious and cost-effective method of combating these threats is by integrating NFC technology.
Contents
What is NFC Technology?
Near-field communication is a short-range wireless communication technology that operates within the unlicensed radio frequency ISM band (industrial, scientific, and medical) at a base frequency of 13.56 MHz, with a typical range of up to 10 centimeters and transmission bandwidth range from 106 to 424 kilobits per second. Unlike radio frequency identification (RFID) — which relies on RF energy or a secondary power source, such as a battery, to power and communicate with devices, NFC is based on inductive coupling. The energy generated by the reader’s magnetic field is used to power the device, and communication between the reader and the target device is then achieved by ASK load modulation of the carrier.
NFC and RFID deliver many of the same benefits and should not necessarily be considered in competition. Rather, the chosen communication method is tailored to picking the right tool for the job. The simplest way to differentiate NFC from RFID is by determining the distance a tag can be read and the technology used to accomplish it. RFID performance is better when reading one or more tags at greater distances. However, the implementation cost of RFID is slightly higher. NFC is written as short-range or localized communication between two devices but can exchange information with multiple devices. Inductive coupling reduces the overall complexity of the design and associated costs.
Comparing NFC and RFID
| NFC | RFID | |
|---|---|---|
| Communication Distance | Short distances (typically 10 cm or less) | Longer distances (typically a meter to several meters) |
| Transmission Rate | ~424 kbit/s | ~106 kbit/s |
| Transmission Method | Electro-magnetic field/inductive coupling | Radiofrequency |
| Wireless Charging | Small devices (1W or less) | None |
| Target Applications | Payment systems (Smart Cards), Public transit (Token, Pass), Authentication (Access, Documents, etc.), Identification (Access, Tracking) | Inventory management systems, Toll management systems, Logistics |
The cost-effectiveness and localized communication make an appealing case for implementing NFC technology into smaller IoT devices. More recently, manufacturers of NFC integrated circuits (e.g., Tagify, HID, Identiv and Seritag) have offered parts with energy harvesting or the capability of supplying power to other external circuitry, such as microcontrollers, sensors, etc. While NFC power harvesting is not a replacement for the higher power of the more widely known Qi Wireless charging standard, it is suitable for smaller devices like wireless earbuds, wearables, watches, etc.
Another benefit of NFC technology is its versatility. When actively communicating, there is always an initiator and target and three different operating modes:
Near-Field Communication (NFC) Operating Modes
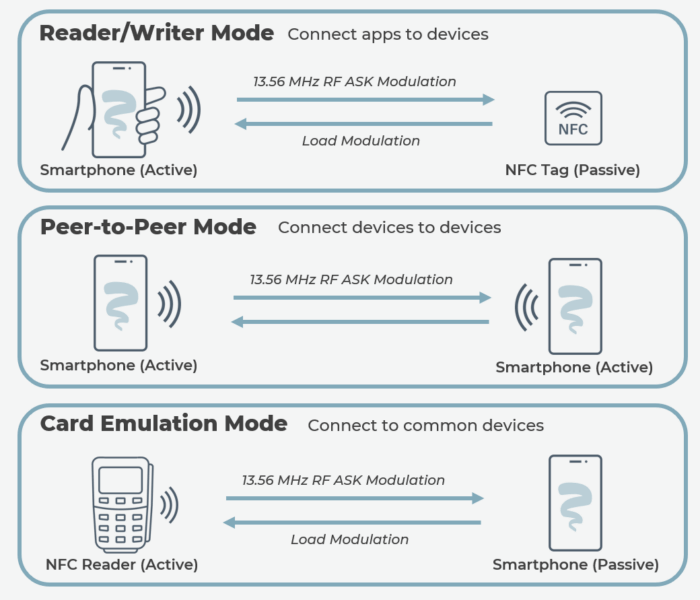
- Reader/Writer: This is the most commonly used, most basic mode of NFC operation, where the initiator supplies power and controls interaction with a passive target. The tag or target draws its power from the electromagnetic field, so no battery is required, circuitry and size are minimal, and cost is ultralow. Tags are integrated in a wide variety of applications, from payment and information exchange using smart card, travel pass or poker chip, to information exchange and access control, including the family pet.
- Peer-to-Peer: Two NFC-enabled devices can exchange data with each other. In this mode, there is a more active dialog between two devices, such as smartphones, smartwatches or other active devices transferring data. Each device is self-powered. Communication alternates the role of initiator and target based on which side is generating the electromagnetic field.
- Card Emulation: This mode combines peer-to-peer and read/write modes. In this mode, an NFC-enabled device emulates a smart card or tag.
NFC and the IoT
In the ever-evolving Internet of Things (IoT) landscape, the security aspects, the effortless device pairing and data exchange between device and tag are important. This can benefit a wide range of IoT applications by streamlining the user experience and making it easier to connect and control a wide range of smart devices — from wearables and home appliances to industrial equipment and beyond.
Possibilities are endless, and there are many innovative ways to enhance the customer experience. The dynamic nature of the exchanged data can provide product-specific information on or about a consumable, such as a bottle or cartridge, to a bridge between different connectivity protocols, such as BLE/Bluetooth, Wi-Fi, and others, enabling effortless device pairing and data exchange.
Moreover, NFC tags are battery-free, interactive devices that can easily embed into or onto a product. The interaction can be transparent or indirect — such as the IoT device with a consumable nearing the end of use and connecting with a service provider — or direct, where consumers can use it with a simple tap. This functionality can extend customer experiences in innovative ways, enabling ongoing interactions and engagements with products even after the initial purchase.
The Real Threat of Counterfeiting and Gray Market Products
Driven by globalization and online sales, counterfeit products harm both brands and consumers. Manufacturers, particularly in the consumer goods industry, face an ever-increasing threat from these illicit and nefarious activities, which can have devastating consequences for their brand reputation, customer trust and even consumer safety.
Often, there may be confusion or misunderstandings about the differences between counterfeit and gray market products. Defining key differences between each is important, as they are going to define how you respond to either or all of the threats.
- Gray market goods: Authentic products imported and sold through unauthorized channels. The products themselves are genuine, but their distribution may violate the manufacturer’s policies. These channels may be legal, but they operate outside the manufacturer’s authorized distribution network.
- Counterfeit products: Imitation goods designed to replicate the appearance and functionality of authentic products. Counterfeit items are intentionally misleading, often produced with the intent to deceive consumers into believing they are purchasing genuine products.
- Black market goods: Items that are illegal to manufacture or sell. Some black market goods are counterfeit, and some are genuine products that are simply illegal to own or distribute.
Counterfeit products can contribute to dangerous business exposure, compromise brand identity and put consumers at risk. The costs associated with this global problem are staggering. According to recent reports, the fake semiconductor industry alone poses a whopping $75 billion risk, while the counterfeit electronics market accounts for another $169 billion. Estimates suggest that the global trade market of counterfeit electronic components could reach up to $1 trillion annually, potentially growing even further. Even worse, counterfeit parts account for nearly 11,000 lost American jobs.
With NFC technology permeating our connected world, it has also emerged as a powerful tool in the fight against counterfeiting and gray market products. Thanks to the economy of scale, many cost-effective semiconductor solutions are available.
Combating Counterfeiting with NFC Technology
Traditional identifiers — QR/bar codes, etched or stamped serialization and other physical identifiers — are of little value in combating counterfeiting today. These solutions are easy to replicate, lack secure data storage and are susceptible to tampering. These traditional physical identifiers do not offer the same level of dynamic, interactive capabilities that newer technologies like NFC provide. By leveraging NFC’s unique capabilities, manufacturers can increase product functionality and implement robust serialization and authentication measures that make replicating their products significantly more challenging for counterfeiters.
There are many advantages of NFC-based anticounterfeiting solutions. Semiconductor tag chip coding and supply chain are highly controlled. Programmed with unique identifiers or authentication algorithms, these tags make it exponentially more difficult for counterfeiters to replicate. Moreover, NFC tags can be designed to offer built-in authentication features, further enhancing security. This approach often includes using secure elements, cryptographic algorithms and other advanced security measures that ensure the product’s integrity and associated data. Additional tag memory areas can be partitioned and read/write access controlled for application data, further enhancing product functionality. Tags are easily embedded into products, packaging or even apparel, verifying authenticity securely and cost-effectively.
Regardless of the implementation method, many challenges still exist:
- Standardized data formatting.
- Automation in manufacturing.
- Enterprisewide management.
Simply put, serialization provides a reliable and secure authentication, but the action or response to an unauthentic product must also be carefully defined.
With the growing threat of counterfeiting and gray market products plaguing our modern world, NFC has emerged as a powerful solution well suited for IoT applications. The unique technology provides manufacturers with robust serialization and authentication measures to protect their brands and customers.
Is Adding NFC Worth It?
Always of paramount concern are the development and production costs associated with adding anything to a design and minimizing bill of materials (BoM). Reader, antenna and tags are highly influenced by volume, materials used, design characteristics and any other customization. It’s not uncommon for a tag to cost $0.15 or less.
Other cost factors also need to be considered:
- Product complexity
- Product cost of goods (COGs)
- Production volume
- NFC implementation/specific requirements
- Design and integration costs
- Testing and validation
- Certifications FCC/NFC forum
- Supply chain management
- Distribution and logistics
However, in the long term, the ultralow cost — for example, as would be used on a consumable product, such as a bottle or cartridge — plus additional functionality make a compelling case for design inclusion when evaluating the return on investment (ROI).
Connect with Cardinal Peak for NFC Expertise
Cardinal Peak is often asked to advise and implement serialization methodologies and algorithms, depending on the desired use case and threat potential — ranging from the most straightforward serial number hidden in flash memory, authentication chips and, in many cases, NFC. Each strategy has advantages and disadvantages, but leveraging NFC’s unique capabilities can help you combat this global issue and maintain customer trust and loyalty. In part two of this blog series, we’ll explore some technical aspects of designing NFC-enabled IoT solutions.
Want to learn more about how NFC technology can benefit your business? Contact our IoT experts for an obligation-free consultation.
Additional NFC and Anticounterfeiting Articles
NFC Blog Post Series
This blog post is part one in a series on near-field communication. Parts two and three are linked below.
- Part 2: NFC Reader Design Essentials: Requirements for Tags and Receivers
- Part 3: Building NFC Readers: Choosing the Right Chip and Implementation Tips
Anticounterfeiting Product Design Case Studies
Check out these case studies for examples of anticounterfeiting products that Cardinal Peak has developed.
